New Cyber Hazard Tutorials
Would you like to know how your staff would react to a real cyber security hazard in their day-to-day life? Are you looking for the benefits of a full-length tutorial in a bitesize format? Look no further. Hut Six is excited to announce the release of our brand-new, unique teaching tool: our Cyber Hazard course.
Looking to train your employees on AI security?
Talk to one of our experts about effective training now.
What are Cyber Hazard Tutorials?
Inspired by hazard perception tests for drivers, our Cyber Hazard series immerses users in short, realistic scenarios viewed through a device screen. High-quality graphics depict web browsers, email applications and more, just as they would appear on your staff's devices. Testing your cyber security knowledge has never been more down to earth.
Users are immersed in a variety of common activities which they are likely to encounter, either at work or at home, such as receiving emails and accessing work documents. And with much more material well on the way, we will have a cyber-hazard tutorial for a wide range of scenarios.
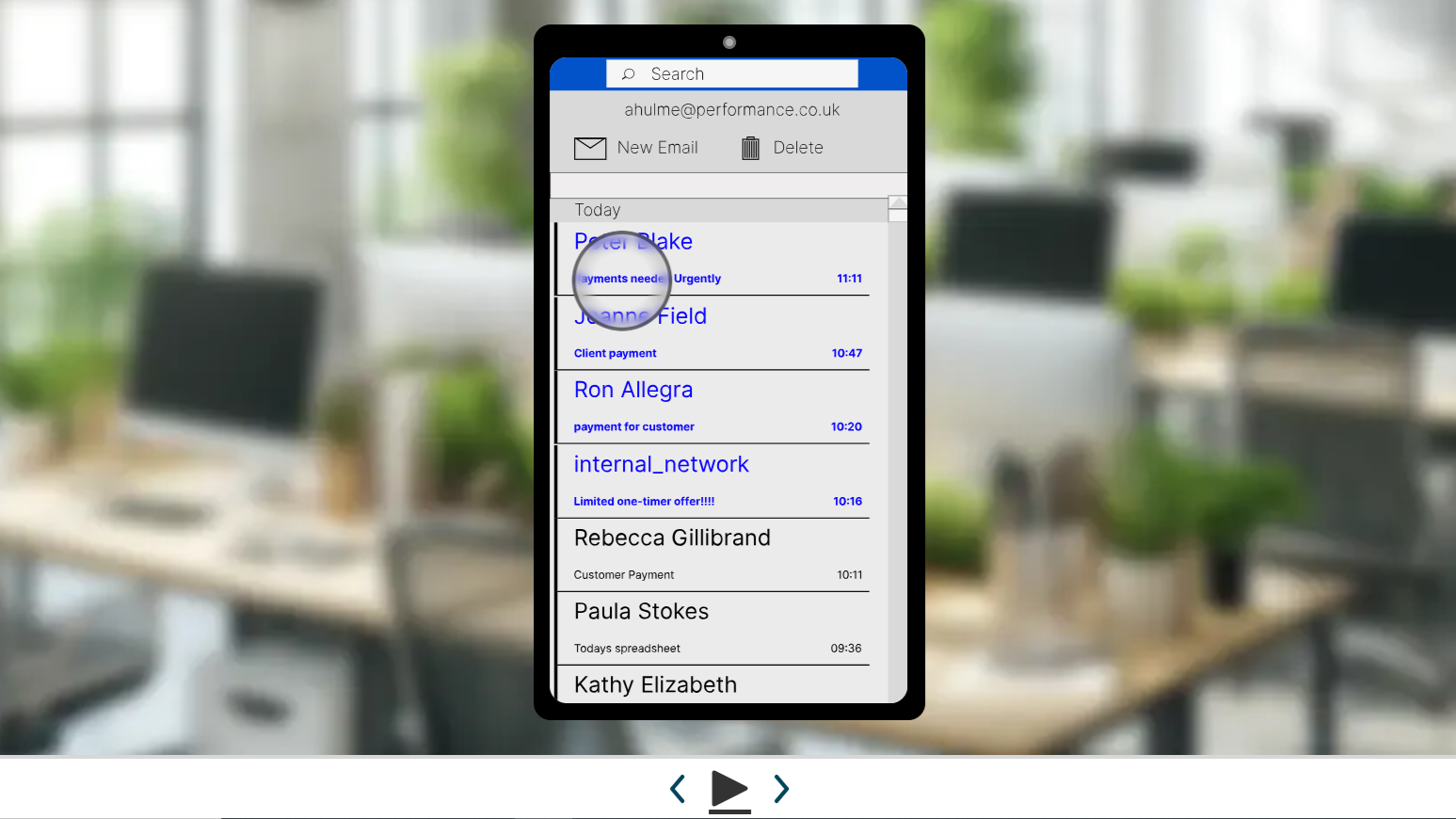
How It Works
An inclusive tool, built with accessibility at the heart, the tutorial is paused at irregular junctions within the scenario and users are prompted to choose whether to proceed or to stop the simulation due to a risk. This ensures they take time to analyse the situation, just as they should in the real world. Hazards are distributed differently in each tutorial, meaning users are kept on their toes, never knowing when to expect the hazard to appear.
The short length of the Cyber Hazard tutorials make them digestible and efficient; the ideal tool for anyone who does not have the time for a full-length tutorial.

Key Features
Realistic Scenarios: Engage users with training in situations they face on a daily basis.
Varied Content: Break the flow of your awareness campaign with some new short form assessments.
Interactive Learning: Users can critically engage with each decision point and live feedback
Time-Efficient: A good way to bring security to the forefront of your employees' mind in-between tutorials.
Employee Security Training
A versatile tool, our Cyber Hazards complement our existing suite of training perfectly, including topics such as phishing, password security and handing data securely.
The course can be employed in different ways:
Reinforce Learning Objectives
If your staff have received any amount of cyber security training, it is important to see if they can apply their new knowledge in a lifelike scenario. With this in mind, you can take Cyber Hazards after a full-length training course is completed and revisit the topics you covered. With realistic depictions of real-life security threats, this is the perfect follow-up to a tutorial, or classroom-based course.
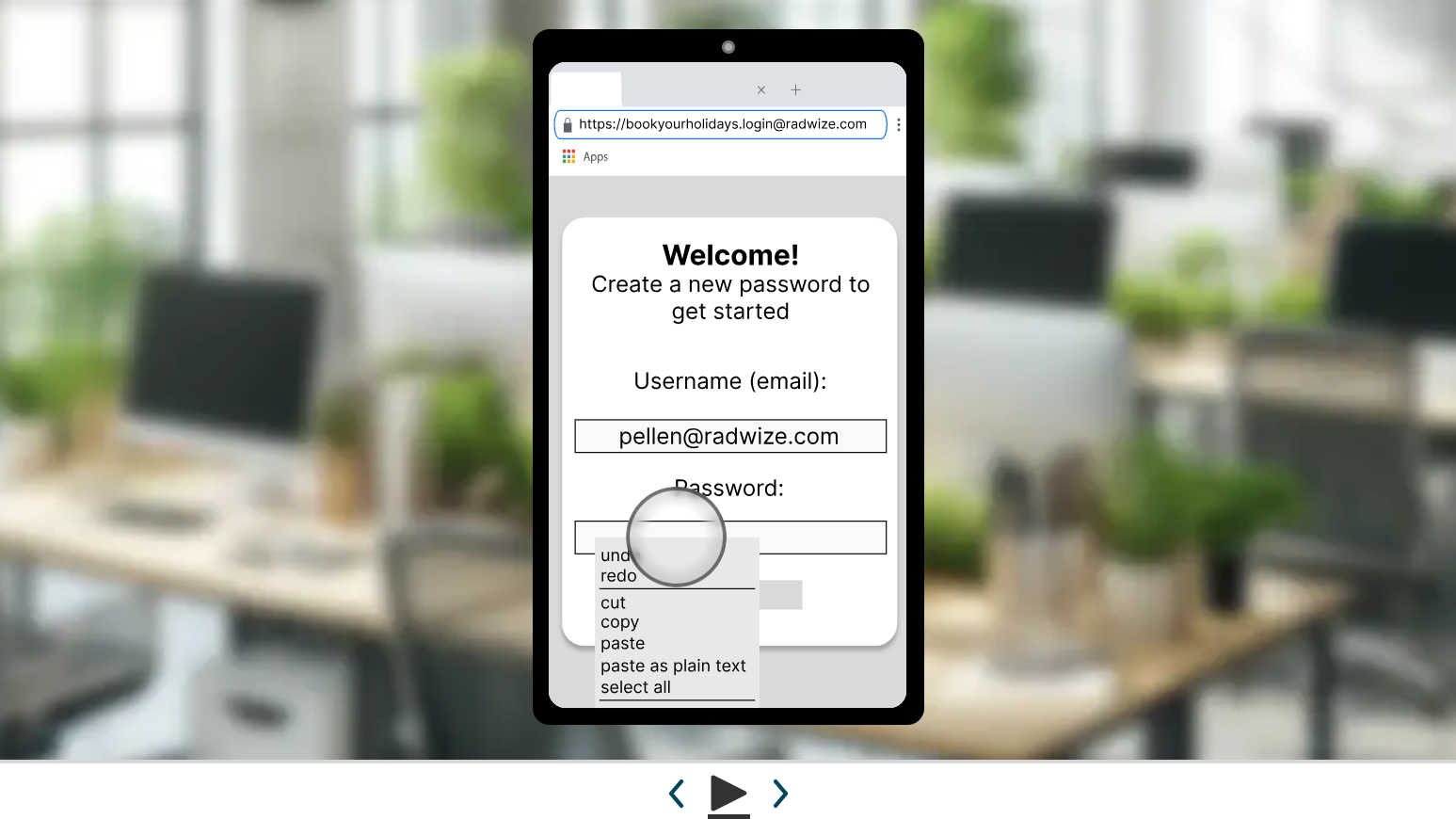
Identify knowledge gaps and Engage an uninitiated audience
Alternatively, you can utilise the Cyber Hazards as a way of preparing for a comprehensive training course. A crucial part of any learning and development process is understanding your team's knowledge gaps, a task for which Cyber Hazards is specifically designed. Prepare effectively and save money and energy by selecting the topics you need to spend time on.
User-Centric Design
Although the Cyber Hazard series is a different entity to our standard tutorials, we have used the same technology to create them. So the dashboard and user interface will look pleasingly familiar to users who have taken our previous tutorials.
The Cyber Hazards course is the very thing that has been missing from your information security toolkit.
Try the new Cyber Hazard Tutorials now by getting in touch with our Sales team!
If you are already a customer, talk to your customer success team today.

Security Awareness for your Organisation
Enjoyed our blog? Learn more about how Hut Six can help improve you security awareness with training and simulated phishing. Start a free trial now, or book a meeting with one of our experts.
Featured
What is the Impact of Security Awareness Training? - Hut Six
Discover the Impact of Security Awareness Training: Prevent breaches, foster culture, & build trust.
What is Personal Data?
Learn about personal data, its types, and significance in data protection. Explore general and special category data, as well as pseudonymised and anonymised data under the GDPR.
Who Does GDPR Apply To?
Who Does GDPR Apply To? And Other Data Protection Questions/ Information Security blog by Information security awareness provider Hut Six Security.
Does ChatGPT Pose a Cybersecurity Risk
In this blog post, we explore whether AI chatbots like ChatGPT pose a cybersecurity risk. We delve into the potential vulnerabilities and threats posed by chatbots, and discuss measures that can be taken to mitigate these risks. Read on to discover how you can ensure the security of your organisation's chatbot interactions.
How Do I Get Cyber Essentials Certified?
Learn how to obtain Cyber Essentials certification and enhance your organization's cybersecurity posture with our comprehensive guide. Our expert insights will help you navigate the certification process to meet the requirements for Cyber Essentials.
Essential Steps for Security Awareness Training
Starting a security awareness training campaign? Here are 5 essential steps to help ensure information security success.
Malicious Insider Threats - Meaning & Examples
Malicious insider threats can cause massive problems. Here we examine some of the motivations behind attacks and methods of detection organisations can use to reduce risk.
5 Biggest Breaches of 2022 (So Far)
Five of the biggest and most significant data breaches, hacks, and information security attacks of 2022 (so far).
Auditing for GDPR Compliance
Questions to consider when auditing your business or SME for General Data Protection Regulation (GDPR) compliance.
Improving Employee Cyber Security
With human error responsible for many breaches and attacks, we offer some helpful areas for improving employee security compliance.












