Security Awareness Training Courses
To make an impact, training needs to be applicable to your organisation specifically. You can easily customise our material to make links, phishing email examples, password guidance and much more match your organisation’s advice.
Our curated induction course instils knowledge while subsequent courses utilise scenario-based decision making to build upon and test users, maturing your security awareness program. You can choose your own training schedule to fit your organisation’s needs and immediate risks.

Explore our curriculum
An Ongoing Training Model with Unique Annual Content
We deliver online cyber security awareness training with multiple years of content that cover all aspects of information and cyber security. Hut Six's courses are all made in house by our expert team of writers, animators and learning designers. Tutorials range from 2 minutes to 10 minutes long and benefits from hundreds of hours of writing, aminations and edits with questions and assessments woven through out to ensure an engaging and superlative experience for your users.
Choose what training you deliver to your team from our wide selection so that they only receive the most relevant security advice. Our training is the most customisable on the market with policy adaptations, custom placeholders, organisations names and logos. Fully bespoke modules are available on request.

Cyber Awareness
The induction course covers all aspects of end user security awareness and is constantly updated with best practice and the latest case studies. Our flagship course prepares your users for the risks they face and builds a foundation of security awareness.
Cyber Command
Playing the role of a Cyber Command agent – a cyber security expert, who helps people in various businesses across the globe – users build upon their Information Security knowledge in scenarios inspired by real-world challenges.
Openmind
In the not-too-distant future, users guide the decisions of various employees at the world’s leading android manufacturer: ‘OpenMind’. Users’ decisions lead to a range of possible outcomes for each tutorial.

Cypher City
Users assist characters through Information Security challenges in a noir-themed metropolis, where not everything is as it seems. In a shocking twist of fate, users must think like cyber criminals to better understand cyber security.
For something short and snappy, try our Cyber Hazard series.
Inspired by hazard perception tests for drivers, our Cyber Hazard series immerses users in short, realistic scenarios viewed through a device screen. High-quality graphics depict web browsers, email applications and more, just as they would appear on your staff's devices. Testing your cyber security knowledge has never been more down to earth.
Cyber Awareness - Induction Course
Start your Training Journey Here
You can see our course summary here or see below for detailed breakdowns of each module. If you have any further questions about security awareness training or our phishing simulator you can book a demo or access a free trial here
Introduction to Information Security
Providing a concise overview of both some of the key concepts of information security, and of what users can expect in their upcoming tutorials, such as the CIA Triad (Confidentiality, Integrity, and Availability).

Using the Web Safely
With browser specific information relating to updates and security settings, Using the Web Safely also looks at URL inspection (scheme, domain, and path) and how to identify and avoid unsafe websites.

Phishing, Don’t take the Bait
Addressing one of the most foundational topics in Information Security Training, this tutorial covers the most common tactics used by online fraudsters for stealing sensitive information.

Password Security
Another foundational security topics, this tutorial not only looks at the underlying concepts of passwords technology, including the methods utilised by attackers, but also at key password management practices that ensure information is secure.

Social Engineering
Equipping users with the knowledge to identify common social engineering tactics and methods is the first step in avoidance.

Physical Security
As an often overlooked area of information security, the physical security of data is essential not only for regulatory compliance, but also for insulating companies from serious security failures.

GDPR: Why it Matters
Establishing some of the basic information and concepts regarding modern data protection regulation, this tutorial is the first of the three tutorials covering the General Data Protection Regulation (GDPR).
GDPR: How does it affect Individuals?
In this tutorial we outline and explain the data privacy rights afforded under the General Data Protection Regulation, as well as some of the broader rules that impact individual rights, and international data transfers.
GDPR: How Does it Affect Organisations?
Covering the essentials of how the General Data Protection Regulation impacts organisation, this tutorial looks at the key principles of common data processing; as well as touching upon storage, information management, and data subject access requests.
Mobile Devices
Applicable not only in a work environment but also in any users’ personal life, awareness of mobile device security has never been more essential.
Malware Protection
Examining the most common forms of malware (ransomware, spyware, etc.), the tactics used by attackers, as well as the significant repercussions of malware infection, this simple and easy to grasp tutorial seeks to equip users with the essential knowledge and skills to avoid the increasingly prominent threat of malware.

Out of Office
For any organisation whose employees travel for work, providing adequate training to mitigate ‘out of office’ information risks is an essential measure.

Working from Home
As remote work is common for a significant number of employees in the modern world, training to avoid the risks associated with working from home is a crucial step for many organisations.

Wi-Fi
Just as information being stored needs protection, information in transit also needs to be kept out of the hands of malicious actors.

Spear-Phishing
Expanding upon the preceding Phishing, don’t Take the Bait topic, this tutorial examines the more sophisticated threat of spear phishing.

Insider Threats
As one of the more complex threat vectors discussed, in this tutorial we looks at some of the more common indicators associated with this notoriously challenging area of information security.
Identity Theft
As an all too common form of fraud, identity theft can have devastating consequences for its victims, financially and in terms of reputation.

Social Media & Privacy
With so many of us frequenting social media websites, threats such as oversharing, lax privacy settings, and the sharing of unverified or controversial information can only be ignored at our peril.

Artificial Intelligence
Artificial Intelligence is a highly useful tool in today’s world but also poses serious information security concerns. Focusing on the most popular form of AI: chatbots, we condense the most important and useful information into one tutorial that teaches users how to use this technology safely at work and at home.
Handling Sensitive Information
Another core concept of information security, abiding by proper data handling procedures is paramount to not only compliance, but ensuring the confidence of clients.

Encryption
Encryption provides much of the fundamental security in our digital worlds, this tutorial presents the information necessary to understand the value of this ubiquitous technology and how it applied in professional environments.
Backups
Along with the confidentiality and integrity of our information, its availability is likewise essential for maintain robust information security.

Printing and Faxing
Although much is made of protecting digital data, adequately protecting physical documents should not be overlooked. This form of risk may be basic, but can serious and devastating consequences in the real world.
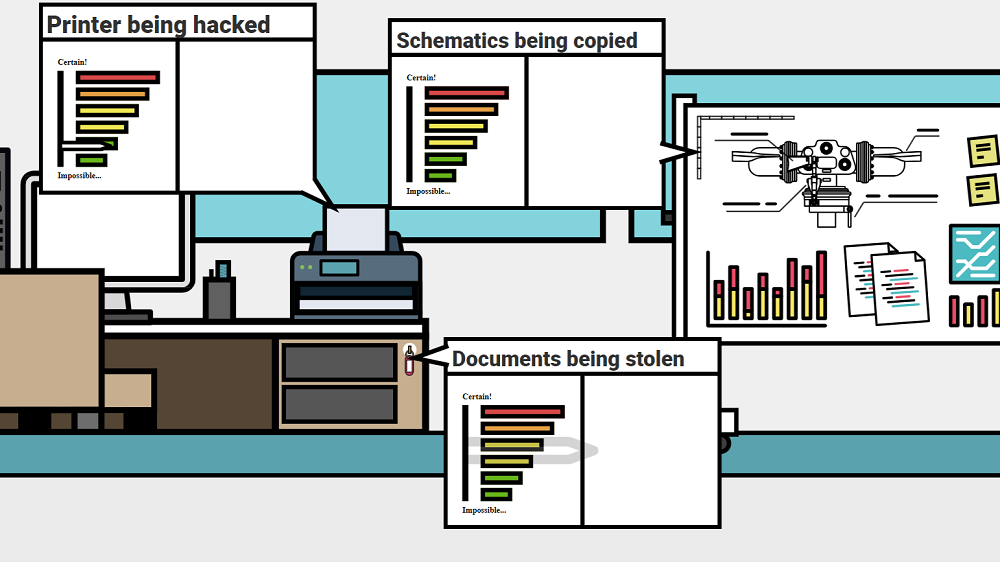
Assessing Your Risk
Risks come in all shapes and sizes, from the foreseeable and minimally severe, to the unlikely but devastating. Each risk requiring a separate response, yet, to avoid and mitigate these risks, they must first be anticipated and understood.

Business Continuity
Continuity planning is an essential for any organisation intent on longevity, particularly in the field of security. As unpredictable as the world can be, foresight and contingency thinking, allows organisations to minimise the likelihood of serious incidents, and should they arise, mitigate the potential impact.

Incident Response
Proper incident response not only helps to ensure that events do not repeat themselves or escalate, but also ensure compliance to current data protection regulations.

Encouraging a Secure Culture
Promoting a secure culture, means that secure behaviour is not simply single events, but a consistent and persistent approach to protecting an organisation’s information.
A Study in Breaches
In this tutorial we use recent and applicable real-world examples of successful Information Security attacks to better understand not only the tactics used by genuine attackers, but also how to mitigate this particular set of risks.
